
How to Figure out All That IP Nonsense Part 1
September 29, 2015
This Week in Getting Hacked: Troll Edition
September 30, 2015In the twenty-first century, we are all likely familiar with the concept of networking. From social networks, such as Facebook and Twitter, to connecting with co-workers and employees on a business network, most of us have used the internet to connect us with others in one way or another. In fact, reading this very article is a way of networking between two people who may be in different countries or even on different continents.
Yes, networking is highly beneficial: it allows global communications to take place almost instantaneously, enables data sharing at rates and levels never seen before in history, and provides new means of socialization and entertainment. But for all these benefits, there are still dangers. Networking, when unsecured, can put threaten the privacy of your data and that of your coworkers and employees.
To protect the data of your business, your employees and your clients, follow these 5 best practices for safe networking. If you don’t, you might suffer a data breach that could negatively affect your firm’s reputation and legitimacy, allow your identity (or that of your employees and customers) to be stolen, or worse.
1. Use a Secure Intranet
While the internet is an indispensable tool and necessary resource for businesses and individuals alike, it should not be used as the primary mechanism for networking. Because the internet is unsecure, data shared across it can be easily seen and accessed by just about anyone.
For example, if an employee logs onto a business server using the public WiFi at his local library, then anyone who is also logged on to that network can see the data being shared, access it, steal it and use it for all sorts of nefarious purposes. Of course, this would first require that remote users be given access to the server. For this reason, we must first differentiate between local area networks and wide area networks:
Local Area Network (LAN): A LAN is network created “locally,” that is, within a small geographic space. It likely will be a single office building, school or other facility that hosts its own networks in which remote users are not given access.
Wide Area Network (WAN): A WAN is a network that moves beyond local borders and covers a “wide” geographic space. It can be accessed by remote users who have the correct credentials to log in.
To secure either sort of network, the business should create an intranet in which employees can communicate, share information and collaborate with more security than would be offered through an internet-based network alone.
An intranet is essentially a private network that is accessible only to a limited number of individuals. It can function as the internet, but the tools accessible on the internet may not be accessible within the intranet depending on what security protocols are put in place. The firm may, for example, use a search engine, design an application for virtual inter-office conversations, and host a number of files or folders. Google, Facebook, Dropbox and other internet-based tools may not be accessible, and their functions may be replaced by more secure tools designed for and by the business.
If a LAN is created, those who have access to it and the tools and data stored within would have to be onsite and access the data directly from the server. The internet may become redundant, and its usage even blocked once the intranet was accessed. On a LAN, blocking access to the internet when the intranet is used may be useful, as it could prevent internet-based hackers and viruses from finding their way onto the server.
This, however, is not as feasible for a WAN, which allows offsite access to the company intranet by employees using the internet offsite. If a WAN is used, there will need to be a greater number of abstraction layers and security protocols in place to protect the intranet and the company data. When networking with remote individuals becomes necessary, then not only will the internal server need to be protected, but a second layer of protection needs to exist. The first would allow the user on the internet to access another abstraction layer that would let them into the intranet. By creating layers of security, the intranet-based network will remain more secure.
2. Use VPNs at Home
If a Bring Your Own Device policy is implemented within the office, local area networks will not be secured by password protections. If an employee picked up a virus while browsing the internet at home, as soon as he enters into the business network, that virus can move from the private device into the business server. Worse, if any data has been saved or cached on the user’s device, a hacker or other intruder might have access to valuable business information without the employee needing to actually be logged into the company’s servers.
Ensuring that employees follow certain safety protocols for personal devices at home can help prevent these things from happening. One of the simplest policies is to require that employees use a Virtual Private Network (VPN) on devices that will be brought into the workplace when at home. A VPN will enable that the data an individual shares remains private and invisible from prying eyes. To function, the VPN takes data being shared on the public internet and encrypts it through a third party server elsewhere so that the origin of the data and the actual information it contains remains unidentifiable.
There are many commercial VPNs available and determining which is best can be difficult. Luckily, Secure Thoughts has ranked some of the most popular, including ExpressVPN, IPVanish and HideMyAss.
3. Design Firewalls with Safety in Mind

Firewalls are the first line of defense and often times the most important when it comes to defending the network. They essentially block all data from entering or exiting a server, file, folder or network except when explicitly permitted. Within a firewall, businesses can design VPNs to act as the gateway into the network, or at least past the first abstraction layer.
For WANs, a firewall of this sort will likely become a necessity. It will enable that remote users remain anonymous when accessing business networks even when using the internet. In this instance, however, a single firewall is not enough. As soon as the remote user enters the server, he should come against another firewall. The first firewall should not permit access into the fortress but should only open a door to another door. Like a castle which has a drawbridge and an iron gate, so too you should view your first firewall as moat and the second as the one that allows the user to begin seeing at least some company data.
It is important to also understand that on both WANs and LANs, firewalls can prevent users from accessing certain sites on the internet. These might include social media sites, pornography/adult-only sites, hate sites or the like. Deciding which websites or types of websites are appropriate for users to access when on the company-based network or when using the business’s private intranet is a decision that must be made on a firm-by-firm basis.
4. Encrypting and Limiting Access to Business Data
If data is sequestered by department or need, then more firewalls may be placed around specific pieces and packets of data, files, or folders. Determining where and how firewalls should be created to protect things within the data’s servers is something that will need to be given consideration. But beyond firewalls, data should be protected internally not just by constructing external walls.
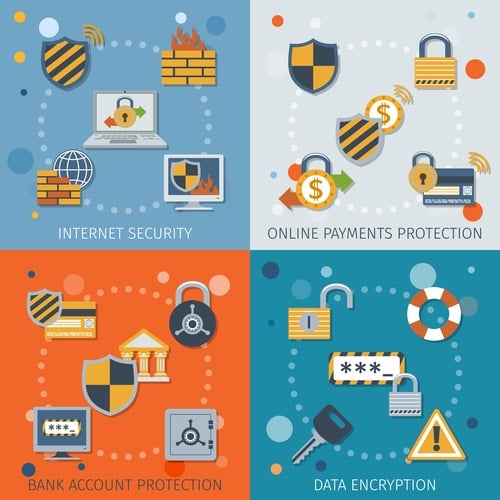
Data encryption is the process by which files and folders consisting of data are “encrypted.” This means that the information or messages within the data are encoded in such a way that only authorized parties can decrypt them in order to access the data and read it. It is a form of internal data protection. If the data remains encrypted, a simple sentence may be transformed into a bunch of nonsensical symbols that wouldn’t be translatable to anyone who does not know how to decrypt the information. Assuring that only users who need access to specific files and folders are given the password for decryption will ensure network safety.
5. Educate Employees about Cybersecurity and Safe Networking
All of these policies may be for naught if your employees do not know why they are being instituted. Safety may mean that employees have do a little more work to access the servers, networks, and data they need. Educating them as to the necessity of these protocols can help them to better understand and even support the new networking safety standards.
This is especially true if employees are going to be bringing their own devices into work. Not only will they need to know about the safety protocols at work, but also those which they will have to follow at home. Giving employees access to materials on cybersecurity, the threats of unsafe web browsing and steps that can be taken to protect one’s self from cyber threats may be the most important and easiest tool to creating a safer network.
Of course, what is included in this material will likely differ from business to business. What do you think should be included in these educational classes and materials? Are there any practices that you use to ensure safe networking that weren’t discussed here. We’d love to hear from you in the comments below!
About the Author: Isa Cox is an internet security expert with a passion for data privacy and secure networking. She enjoys sharing tips with cutting-edge employers who want to offer a flexible work environment to their employees.
1 Comment
Hi,
Very nice post defining networking. I absolutely love this website. Thank You.