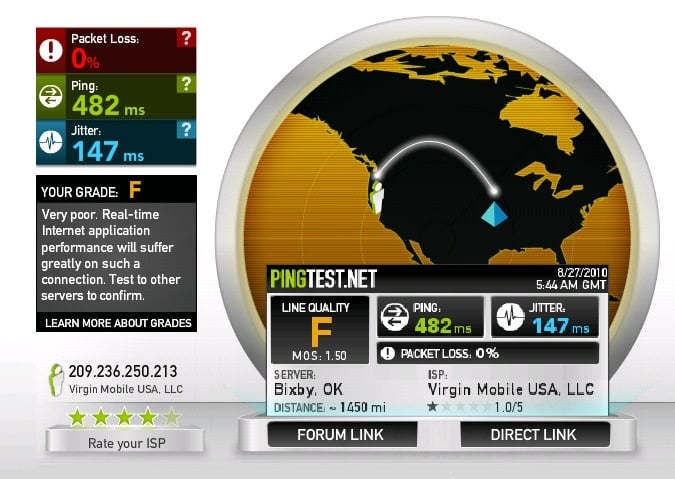
How to troubleshoot a network Timeout
October 28, 2013
UPDATE: Co-location Demand Hits Stride in Australia
November 3, 2013Like any other network, Voice over IP networks are vulnerable to malicious attacks.
VoIP crime is a serious threat to VoIP providers. Although many thought the days of Phone Preakers died with VoIP toll fraud, identity theft, and malware specific to VoIP is out there.
 Edwin Pena was recently in the news for being the first person to be caught and prosecuted for VoIP hacking.
Edwin Pena was recently in the news for being the first person to be caught and prosecuted for VoIP hacking.
Working with another hacker, Pena was successfully able to steal VoIP minutes from major VoIP providers, including Net2Phone, NovaTel and Go2Tel, and charge them to his own VoIP “company.” He charged lower rates because he was stealing service, not providing one.
Although it’s always good when a criminal is brought to justice, he managed to cause $1.4 million in losses from his victims. Here are some steps you can take if you are a VoIP provider to protect yourself from attacks and toll fraud.
1. Subscribe to an IP Hacker Address/Phone Number Blacklist –
If a threat is identified by one organization, it is paramount that this information be spread before more damage can be done. Many IT companies and Asterisk support providers have access to common lists of known threats. These lists are also shared with authorities like the FTC and FBI, that investigate the people behind the addresses. These lists ensure that the number of people and businesses affected by hackers remains small.
2. Use a trusted Colocation Center with high level of security –
Colocation facilities are large data centers in which several ISPs, Telcos, and cloud service providers all house their respective equipment. The equipment, in turn, may be connected physically with copper or fiber rather than through Internet protocol. One of the primary advantages of a colocation facility, or “colo,” is that the colocation facility may provide added value. One such value is physical security. Technicians and security guards will pro-actively walk through the halls and keep watch for any attempted or successful tampering.
3. Require hardware registration for softphones –
A soft-phone is a software that connects to the VoIP network. The user typically uses a headset and makes calls normally. But there is a hidden danger to this convenience. Hackers can discover how to log in remotely through devices that do not belong to subscribers. By requiring subscribers to register their device’s MAC address in order to use the softphone, providers can easily cut down on fraud.
4. Be vigilant against outright theft –
Hackers have been known to go straight to the financial arm of big companies. One CFO of a cloud service provider was in the process of transferring $180,000 when a series of pop-up ads exploded on his computer. An unauthorized transfer for the same amount was being sent to Hong Kong. He immediately snapped into action and was able to recover the entire amount.
5. Separate data and VoIP network traffic –
By having two discrete VLANs, you have a natural firewall between the two. Therefore, attempts to send malware over VoIP will be less likely to succeed.
By: Reuben Yonatan – CEO and Editor-in-Chief at GetVoIP & CloudHostingHQ
