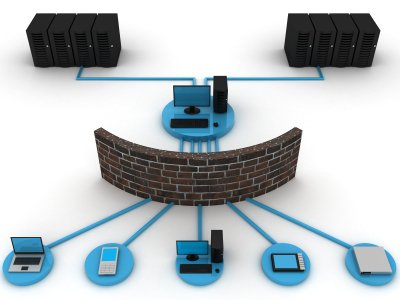
Critical Importance of Good IT Infrastructure: Part One
April 11, 2012
The Future of Broadband Speeds Around the World
April 13, 2012So in part one we introduced the subject of good IT Infrastructure, discussed key questions and defined the backup in detail. For part two we will be exploring deeper into the planning phase and encryption methods.
How to Plan for the Future Issues
The way to plan for future issues comes with identifying the methods that attackers generally use. Most of these will be the weak parts of the security system that is already in place. Typically, they will take advantage of those vulnerabilities left open by IT admins working on a company’s dedicated hosting servers. Evaluate the tools that attackers use for their method of attack. Any business must have counter-measure tactics in place to help combat the tactics that can cause harm to your server and valuable information.

Steps should be placed in the gates of security on the IT steps as much as the physical security of doors demand. This can be achieved through passwords that must be used for access to everything on the computers. That way there is a trail of employees access to valuable information. This can be valuable if a crime should occur. The systems or IT Administrator will set these initial passwords in a secure encryption for the staff. Then, the staff must create their own passwords. Make certain that the staff knows to use a password of at least 13 words and letters in a combination that adds at least on capital letter.
These steps will help prevent the common problems. They can all be averted and the team can create a safer system for your business. Remember to have the staff change their passwords at least once a month for safety. There is one further step that can be added to help the security further.
Government Grade Encryption
The government grade encryption is available for those businesses that feel that their safety should be taken one step further for protection. Devices called encryption keys can be purchased for the IT department that will encrypt the system user every time they log on. It creates a password for their password.
Those keys are very expensive, so it is important to reflect on one of the original questions. The cost must be effective for the department to justify the cost of implementation of encryption keys. If the money does exist, then this is by far the safest route for security to avoid common security issues.
The importance of this scalable IT good infrastructure is the way that any business can establish a safer set of practices for security. This should be re-evaluated at least once a year after it is put in place.
Once completed, this system will help prevent the problems that are common for sound business choices. Cloud computing can help place the business safely on the cloud. Keep it easy to safely use so your business continues to grow.
Author Bio: Frank writes on behalf of a number of businesses who have addressed security concerns such as these and many more. Frank typically writes about technology, social media and up and coming business subjects such as auto enrollment

