
This Week in Getting Hacked: The NSA Knows Your Face Edition
June 23, 2016
The Past, Present, and Future of AI Chatbots
June 29, 2016For most companies, cyber security has always been about keeping criminals out of their data centers with the best firewalls money could afford. Firewalls are great, they can keep most of the criminals out, but not all of them. It’s only a matter of time until a hacker is able to figure out how to get past the most recent firewall update. Then it turns into a game of cat-and-mouse, as the IT team struggles to update their firewalls, and the criminals find new ways to sneak through them.
The problem with this model is, once a criminal is able to get past those defenses, there usually aren’t many security measures blocking them from moving around the network completely undetected.
In order to remain undetected, hackers use “east-west” traffic, or server-to-server traffic within the data center. Hackers have learned not to leave the data center to access another network or anything outside the data center. Instead, they are able to stay within the system for months on end, simply by avoiding the main security measures. During that time, they can be gathering important information or creating millions of other problems.
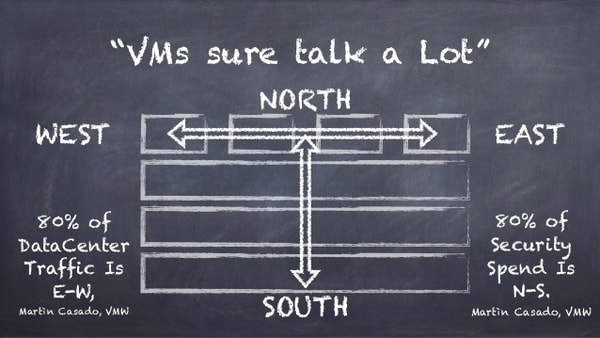
Photo Credit: slideshare.net
These east-west paths were created to lower latency in the data center, and because it would be difficult to prevent threats with firewalls alone. So, most companies have not implemented many blocks for east-west traffic, instead, they have focused all their efforts on the “north-south” traffic, through the gateway.
Protecting data centers with firewalls, without trying to detect the criminals who sneak inside, means that most companies don’t even know their network has been hacked until the hackers are long gone and their data had already been comprised.
Why is Cyber Security So Important?
A recent report by CIO found that half of the professionals say that the loss of data is their top IT security risk. That’s because the average data breach in 2015 cost a company $3.79 million dollars, which translates to a loss of around $500 billion dollars around the world annually. By 2019, the cost is predicted quadruple to $2.1 trillion globally.
As businesses rely on their data centers to store more and more of their valuable information, there will be greater and greater threats to those data centers, and thus, a need for newer and smarter security methods to stop them. Here are three examples of new security measures that data centers are taking to detect attackers and prevent them from attacking in the first place.
Focus on the Threats with Cisco’s FIREPOWER
The Cisco Firepower won this year’s Interpop security award with their next generation firewall (NGFW), which claims to be the industry’s first ‘threat-focused’ NGFW.
The firewall is able to detect threats by understanding how normal users are connecting to applications, and comparing that information with threat intelligence. The threat detection allows businesses to identify and stop threats before they become any more serious.
David Goeckeler, senior vice president and general manager at Security Business Group, Cisco explains that the Firepower allows for “better protection, and faster detection and response to advanced threats. [It] will help our customers build a dynamic, resilient secure infrastructure to combat threats in real-time”
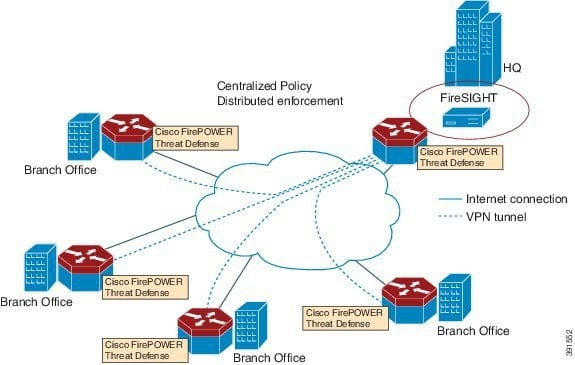
Photo Credit: cisco.com
In addition, the NGFW is able to unify the management of all firewall functions, from application control to threat prevention and malware protection throughout a management console, making it a lot easier to manage your firewalls across the network.
Analyze your data center’s weaknesses with ASAP
This year, the Cyber Defense Magazine InfoSec awards named Illumio’s “Attack Surface Assessment Program,” (ASAP) the most innovative data center security solution of 2016. ASAP is an advanced algorithm that generates a map of all your data center activity and identifies all of the active and inactive pathways.
Nathaniel Gleicher, the former Director for cyber security policy at the White House, developed the program for Illumio. He says it allows users to analyze the traffic in their network, their applications, their environments, their servers, and how each of the separate parts communicate with each other.
In their two-step program, Illumio gives a business a simple script to run, which generates a roadmap of all the data center activity. Then, Illumio analyzes the data, and presents the business with a detailed report on all the weak points within the network, identifying the most likely areas an attacker could infiltrate. ASAP gives businesses the power to understand their network and the best places to defend against an upcoming attack.
Nathaniel Gleicher explains, “One of the challenges is that the attack surface can be so vast. If you try to secure everything equally, you often end up not securing everything enough,” Gleicher said. “You need to prioritize security around your most valuable information.”
In addition, ASAP can also detect where a malicious signal is coming from, and quickly allow the IT team to isolate and quarantine the server the connection is coming from. This would allow a business to stop a cyber-attack in progress, and provide the business with a lot more information about the paths that cybercriminals are utilizing, making it much easier to stop a future attack from the same paths.
Trust No One with VMware NSX & Micro-segmentation
Traditionally, businesses have segmented their networks with physical firewalls and routers, which were able to control traffic between web tiers, application tiers, database tiers, and the internet. But, all these firewalls made life difficult for IT teams. It was time-consuming and confusing to implement even small changes across a large network, and, in the end, they didn’t do a very good job of stopping breaches in the first place.
With the advent of software-defined data centers (SDDCs), companies were finally able to write software that catered to the needs of their business. Not only can micro-segmentation detect threats from anywhere within the data center, it can also create and change security policies automatically, all while matching the speed and complexity of the workloads they are protecting.
Micro-segmentation can give a zero-trust level to every individual workload, which means cyber criminals can no longer piggyback on legitimate users, or hide in the dark corners of your data center.
As it is described in the White Paper, Micro-Segmentation Builds Security into Your Data Center’s DNA, “physical security (with firewalls and routers) is like using gloves to guard against germs. It is external, limited protection (if someone sneezes in your face, you’re probably going to end up with a cold or flu). Micro-segmentation is like fortifying the immune system of the data center: germs (or malware) can’t get it.”
In addition to protecting the information on data centers, Micro‐segmentation also enables companies to use the security measures of the SDDC on their desktop computers and mobile environments alike.
Why the Future of Cyber Security is Holistic
Firewalls have their problems, but they are not going away anytime soon. However, future businesses are not going to rely solely on their walls to protect them from outside invaders. They can now keep a few guards inside of the walls to protect them in case an attacker ever gets inside.
