What Is the “Splinternet”?
November 15, 2022
What Is Robotic Process Automation?
November 23, 2022‘This Week in Getting Hacked’—the world’s greatest cybersecurity-related link dump! Each week, we bring you the best news stories from the cybersecurity field, letting you know who’s getting hacked, who’s hacking, what data is leaking, and about what you should take with caution. So strap in, change your password, and let’s find out who’s getting hacked this week!
On to the links…
Week of January 9, 2017
A Twitter account associated with WikiLeaks—everyone’s favorite “we swear we’re transparent” information source—claims want to publish the financial and familial ties of all Twitter verified users. Since then, the tweet has been deleted, which is good news, considering it’s pretty much doxing hundreds of thousands of people, many of whom probably don’t want that information disclosed.
The account attempted to cover their tracks by claiming that they wanted to just explore influences based on proximity graphs.
Speaking of WikiLeaks, here’s the full US Intelligence Community report of the Russian meddling in US elections. Remember when WikiLeaks only released information about one side and claimed it wasn’t political in nature, despite there being overwhelming evidence of potential conflicts of interest on the eventual winning party that would kind of help their whole “we don’t choose sides, just transparency” thing? Me too. This is the declassified report that was gathered by the US IC, as the classified report shows all the evidence they have, and revealing that would compromise the ways they were able to obtain it.
Keeping on the US election topic, the Homeland Security Secretary Jeh Johnson designated the US election voting infrastructure as critical, saying that recent attempts to influence or manipulate our democratic elections is cause for concern and increased security.

Photo Credit: Linked Above
Here’s a quote:
“Given the vital role elections play in this country, it is clear that certain systems and assets of election infrastructure meet the definition of critical infrastructure, in fact and in law…”
That’s pretty cool, and also kinda concerning that we didn’t consider that as an option before today.

Photo Credit: Linked Above
What is concerning, however, is that the government may have been paying Best Buy Geek Squad employees as informants to search through computers and other devices you may bring in to be repaired or checked. The information came out in a court case, United States of America v. Mark A. Rettenmaier, where a California resident took his computer to Best Buy because it didn’t start, and the Geek Squad technician found child pornography on the device, and alerted his boss, who was also an FBI informant. The evidence was found via a carving tool, which digs through old and deleted files for certain content, which should not be used when attempting to get a computer to start, as per the customer request. Best Buy has denied their involvement with the FBI.
And finally…
If you use the AutoFill function on your browser to fill out information fields, there’s a chance you’re giving up your personal info unwittingly, as malicious sites will use hidden text boxes to gather than information.

Photo Credit: Linked above
So, you know, change your password and definitely don’t use AutoFill on your browser.
Week of January 16, 2017
If you’ve ever hired a developer for a website or a project, hopefully you did a little bit more vetting than the thousands of people that hired a Dutch developer, as he installed backdoors into nearly all the websites he built for clients.

He used the backdoor to gather customer information and use that info to open gambling accounts and extort victims and their families for money. If I could steal a line from Austin Powers: Goldmember: “There’s only two kinds of people in this world that I hate. People that are intolerant of other people’s cultures, and the Dutch.”
After numerous lawsuits, cases, and denials, a pacemaker vendor admits that maybe—JUST MAYBE—its hardware can be hacked. Here’s a statement from the FDA on the St. Jude Medical pacemaker:
“The FDA has reviewed information concerning potential cybersecurity vulnerabilities associated with St. Jude Medical’s Merlin@home Transmitter and has confirmed that these vulnerabilities, if exploited, could allow an unauthorized user, i.e., someone other than the patient’s physician, to remotely access a patient’s RF-enabled implanted cardiac device by altering the Merlin@home Transmitter. The altered Merlin@home Transmitter could then be used to modify programming commands to the implanted device, which could result in rapid battery depletion and/or administration of inappropriate pacing or shocks.”
If you’ve ever wondered how Google Play is able to vet its apps for malicious content, it’s an algorithm combined with Android’s own Verify Apps program that then checks the app for malicious stuff, as well as how long a user retains an app.
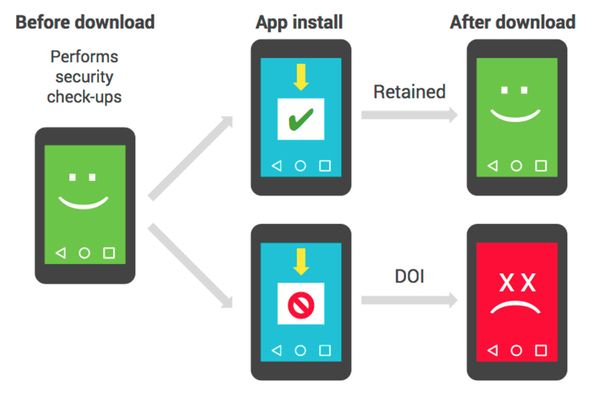
If it drops below a certain score, goodbye app.
Rudy Giuliani was announced as now-President Trump’s cybersecurity adviser.
The only problem is that his website about his security team is unsecure and extremely vulnerable.
Google released a security document that reveals the measures they take to ensure the security of their hardware and products. Unfortunately, in that document, they let slip that they install a custom security silicon on all of their servers, even the ones they colocate. The silicon chip “allow us [Google] to securely identify and authenticate legitimate Google devices at the hardware level.” I don’t know how to feel about this, but I understand where they’re coming from.
And finally…
–The CIA dumped a BOATLOAD of declassified files onto the Internet the other day for your reading enjoyment. Here’s something to note:
“Included in the database are US discussions about assassinating Fidel Castro, details of Nazi war crimes, reports of UFO sightings, and a study into human telepathy dubbed “Project Star Gate.”
YEP I KNOW WHAT I’M DOING WITH MY WEEKEND.
Week of January 23, 2017
Are you using Incognito Mode on your browser, or employing other privacy-hiding protocols to anonymize your actions on the Internet? Turns out, it might not be so private or anonymous. A study shows that even if you go full “anonymous”, sites and services like Google and Facebook are already tracking your actions, even if you set your privacy settings to the max and use anonymous browsers. My favorite part of that article is the author’s use of “de-anonymizationer”, which sounds like a sci-fi weapon designed to shrink you or something.
Speaking of privacy, there’s going to be a new battle in the war of staying out of my sh*t with “always on” devices like Amazon Echo, Google Home, and more.

Who is that data being sent to? When is it being recorded? Who has access to it? How can we be assured that the microphone isn’t recording at all times, despite the companies saying it isn’t? What happens with this data if law enforcement ever gets involved?
Donald Trump’s pick for Attorney General, Jeff Sessions, wants to allow cops to have encryption backdoors for devices and platforms. That’s not cool, especially since the federal government can’t even keep their own stuff from getting hacked. By granting agencies a backdoor, you’re opening your customers up to other threats, because now there IS a way in. Asked whether encryption is important to national security and the security and privacy of the American people, Sessions responded:
“Encryption serves many valuable and important purposes. It is also critical, however, that national security and criminal investigators be able to overcome encryption, under lawful authority, when necessary to the furtherance of national-security and criminal investigations.”
Speaking of “ways in”, the open door that is Yahoo is under investigation from the SEC for taking so long to report the massive data breaches that left over a billion users’ info right out in the open. This new investigation doesn’t bode well for the sale of Yahoo to Verizon, who are already looking to renegotiate the $4.8 billion they originally agreed to pay for the former search engine.
That hacker who leaked nude photos of Jennifer Lawrence and other celebrities has been sentenced to jail for nine months. The hacker, Edward Majerczyk of Illinois, had his lawyer argue that while he illegally hacked into their accounts, he was initially doing it for his own personal portfolio and private viewing.

Ahh, he’s like the pervert’s Robin Hood.
And finally…
Symantec has revoked a boatload of security certificates that were mis-issued after a being exposed by Andrew Ayer, a certificate vendor. Symantec responded:
“The listed Symantec certificates were issued by one of our WebTrust audited partners. We have reduced this partner’s privileges to restrict further issuance while we review this matter. We revoked all reported certificates which were still valid that had not previously been revoked within the 24 hour CA/B Forum guideline – these certificates each had “O=test”. Our investigation is continuing.”
Security: it’s almost always unsecure!