
Friday Fun Blog: High-Definition Space Edition
November 4, 2016
Come Together, America
November 7, 2016and How to Avoid the Same Happening to You
In the weeks before the presidential election, thousands of hacked Democratic emails have been published by Wikileaks. These leaks could have the potential to change the outcome of the 2016 elections, and, possibly, the future of American politics.
It all began on July 22nd, just three days before the Democratic National Convention in Philadelphia, when WikiLeaks published the largest leak to date; nearly 20,000 hacked emails from the Democratic National Committee (DNC) were released in less than a week.

Then, on October 9th, thousands of emails from Hillary Clinton’s presidential campaign chairman, John Podesta, were also released. As of this moment, there have been 43,104 of his emails published on Wikileaks, with the promise of more to come.
There’s a lot of speculation on where the emails came from, and what impact they will have on the election, but perhaps the question we should be asking is: how were these emails stolen in the first place, and what can we do to avoid the same fate?
How the Clinton Campaign and the DNC Were Hacked
According to Reuters, the FBI had been investigating a cyber-attack on the DNC’s servers for months before they finally told them to “look for signs of unusual activity” on their network.
The DNC did not find anything until May of this year, when they finally called in the private cybersecurity team, CrowdStrike. When CrowdStrike took a look into the DNC networks, they immediately identified two different hacking groups that were busy stealing thousands of documents.
Later, when Podesta’s emails were hacked, another cybersecurity team called SecureWorks Counter Threat Unit (CTU), found the same two hacking groups were stealing documents from the Clinton Campaign.
But, how were these groups able to breach these networks in the first place? The answer comes from the very emails that were hacked.
Spear-Phishing
On March 19th, John Podesta received a very common email from Google, notifying him that someone had used his password to sign in from a different computer.
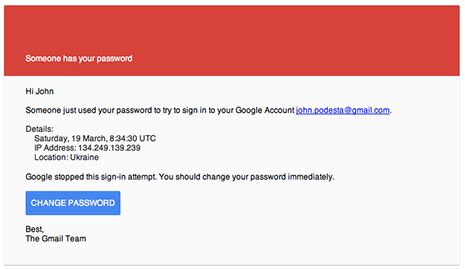
The fake email notice that targeted John Podesta
The problem is, this email didn’t come from Google at all—it was a phishing scam from hackers in Ukraine.
Phishing scams are emails that trick people into giving up their private information (passwords, bank accounts, credit card numbers, etc.) These emails are usually very broad, as they are sent out to as many people as possible. Whereas spear-phishing scams are only sent to one person at a time, so hackers can use more specific and personal information to fool their target.
It is very common for people to open emails like this, especially when they come from a trusted source like Google. In fact, cyber security company FireEye has reported that 70% of people will open a spear-phishing email, and, of those people, 50% will enter personal information or click on a malicious link.
That is why it is so important to check the source of your emails, no matter where they appear to come from. If you are weary of an email for any reason, you should always ask a member of your IT department before opening any attachments or clicking on any links.
Hidden Links
Podesta’s team was smart to ask their IT department about the email, but, apparently, they were not smart enough to spot that the email was fake. And it would not have been very hard for them to see that the link in the email was actually a Bitly link.
Bitly is a popular URL shortener that is prominently used on Twitter to shrink long URLs into just a few characters. According to Bitly’s statistics, the link that was sent to Podesta was clicked twice in March.
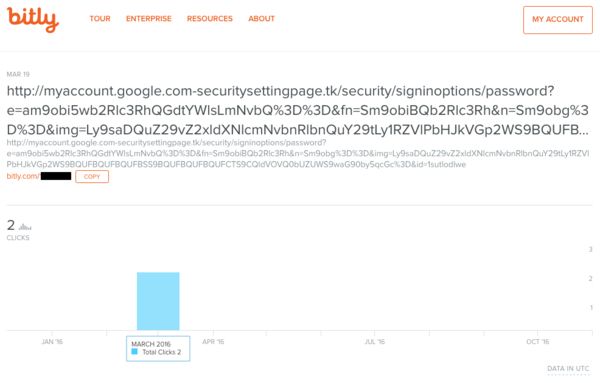
Bitly’s own statistics that show the shortened URL sent to Podesta
Bitly makes it very easy to hide links, but it is just as easy to discover the real URL by hovering your mouse over a link, which should make the destination URL appear on the bottom of the window in most browsers.
Or, if you want to be really safe, don’t click on any links at all. You can always type the URL into your browser manually. This way, you will never be tricked into visiting a spoofed web page.
Stolen Passwords
If Podesta’s team had checked, they would have seen that the Bitly link was hiding a very long URL. This long string of alphanumeric characters was, in fact, encoded with John Podesta’s personal information. It was that information in the actual URL that was used to populate the spoofed Google login screen and made it look so authentic.
The spoofed login page prompted Podesta to enter a new password, which went straight to the hackers. With his password, the hackers could gain access to his email account and any other accounts he used that same password for.
That is why it is also important to use different passwords for different sites. If you accidently give one password to a hacker, and that is the same password you use for other accounts, they will be able to gain access to every account that uses that password.
If you have trouble remembering passwords, you can use a password manager like 1password or LastPass, which will generate and store strong passwords for every site you visit.
Malware
These spear-phishing emails not only stole passwords from the Clinton Campaign and the DNC, they also download malware (malicious software) onto their computers. There is not much we know about the malware that was downloaded, but there it seems to have allowed the attackers permanent access to their entire network, and even allowed hackers to take over their computers.
Anup Ghosh, CEO of the Invincea cybersecurity firm, studied the malware on the DNC systems, and concluded that the hackers:
“Essentially got the DNC to download malware which let them remotely control their computers.”
If you want to protect your network from malware, you need to download an antivirus or antimalware program. There are many different options, but you can compare and contrast here.
What Can You Do to Protect Yourself from Getting Hacked?
If you don’t want to be like Podesta, you can protect yourself from spear-phishing attacks with a few simple steps:
- Always be vigilant of emails, even if they come from trusted sources.
- Never give your password to anyone unless you know where it is going. And make sure to use lots of different and complex passwords.
- Check URLs that you receive in emails, and, if you can, enter the URL directly into your browser rather than clicking on a link.
- Do not download any attachments unless you know where they come from, and have a good anti-virus / malware program installed on your computer.
For more information on how to protect yourself from spear-phishing attacks, you can also try one of our dedicated servers. It not only keeps your emails safe from hackers, you will also gain a fast and reliable network from one of our 22 locations across the US.
*Main photo credit: wikileaks.org
