How to Prepare Yourself for the Hidden Costs of VoIP
August 28, 2014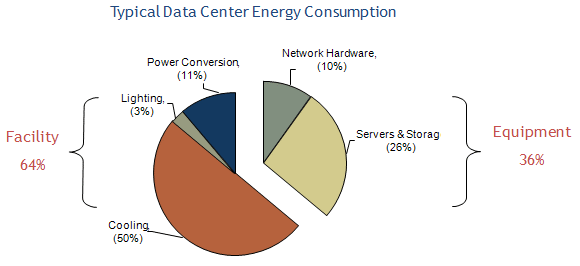
Are The United States’ Data Centers Wasting Energy?
September 3, 2014

If you haven’t heard by now, your everythings on Apple’s Cloud Storage system, iCloud, is not safe.
Do you hear me!? Not safe! Abort! Jump ship! Delete everything that you hold near and dear because the hackers are coming!
Over the Labor Day weekend several A-list celebrities, including Jennifer Lawrence and Kate Upton, had numerous, how do we say “provocative,” images leak to the public.
The media-storm that followed was soon proceeded by PR people and copyright agencies quickly trying to delete the images forever.
As we know from Beyoncé’s Super Bowl “Hulk” images, the internet is a thick Bogland of desolation and mire—so good luck with that.
What Are The Dangers of Cloud Hosting?
But before you make the jump to Android to protect yourself from any embarrassment, let’s take a look at the real problem here: Cloud security.

Coined “CelebGate” by the masses, this Hollywood scandal indeed did leave the “gate” wide open to the cloud network which hosted iCloud.
Speculations abound about how/when the hack occurred, but they did and that’s what matters.
And let’s get down to it, the cloud network is a shared network and—dare I say—something like this was bound to happen, right?
The Storminess of Cloud Hosting
As mentioned above, the Cloud, since it’s shared, leaves itself more vulnerable than, say, a dedicated server.
One of the reasons is due to something called resource pooling.
That basically means that computing resources are shared between all service users. That means that if you’re using a cloud service like iCloud, your information is stored alongside other user’s information as well. And you’re all using the same resources.
This means that in the event of a potential server hack—all the information on that server could potentially be viewed, downloaded, etc.
Let’s think of it as an actual cloud (I know, it’s difficult to imagine). Every water droplet is a user’s data. If the cloud gets too full, you need to pay for the cloud to get larger (okay, that’s not how actual clouds work, but bear with me). But let’s say the cloud just can’t take anymore. What do they do? They burst and rain (your data) starts to fall all over the place (internet).
That’s basically what happened here.
One crazy guy in his dark basement with his 60 oz. cup of soda somehow managed to force his way into iCloud where he was able to sail the skies jumping from one “cloud” to the next.
How Can You Protect Yourself From Cloud Vulnerability?
But, let’s say you use other means of storing your data, like a dedicated server.
In that case, your data is stored by itself in its own personal castle, complete with a moat and several of the kingdom’s best knights along with those spiky walls.
That’s not to say a stronger, purely evil lord cannot breach your walls, but it’s a lot more difficult.
So before you take the pic, just be sure you know where it’s going and please be sure you know the risks involved with any kind of internet storage.
For more information please contact QC Crea
