This Week in Getting Hacked: Access Denied Edition
February 17, 2016
Colocation America’s Great Computer Tools Series: Websites
February 19, 2016In a recent security report, Cisco revealed that merely 45 percent of organizations or businesses have true confidence in their digital security posture. In other words, less than half of all organizations polled indicated that they are confident in their level of security – security which is protecting sensitive internal data from leaking, as well as that of their customers and clients. Needless to say, this is concerning for many reasons, but certainly understandable.
A massive rise in high-profile hacks and sensitive data leaks has shown us all that digital security is no joke. Cisco’s report comes right on the heels of a K-mart announcement claiming it’s experienced a security breach. They’re far from the only ones – other organizations that have experienced breaches include Target, Ashley Madison, Sony, the IRS, VTech and many more.
Anthony Stitt, the Australian and New Zealand security expert for Cisco, believes that this decline in confidence is because software vulnerabilities are proving more difficult to patch than ever:
“I think the declining levels of confidence that we’re seeing is in response to the fact that the number of software vulnerabilities that are appearing every year seems to be growing and that an organisation’s ability to even do fairly as basic patching seems to be declining over time. Compromises happen, breaches happen, but what’s the organisation’s level of preparedness to be able to deal with that quickly and easily? Because certainly the number of vulnerabilities are not going away – an organisation’s ability to patch and keep criminals out doesn’t seem to be working.”
According to Trustwave Holdings, 98 percent of applications scanned for problems were found to have one or more vulnerabilities.
With the right amount of time, it’s not particularly difficult for unscrupulous individuals to take advantage of these vulnerabilities, many of which have not yet been discovered by official IT or security experts working for the affected organization.
For example, the IRS didn’t announce until May 2015 that tit was able to close a security hole which had been open since February of that same year. All that time, it was being used by hackers to gain sensitive information. More than 300,000 taxpayers were affected, as fraudsters stole info like names, Social Security numbers, addresses and more directly from the IRS website. This is a government agency we’re talking about here, one that is responsible for not only protecting the taxpayers it services, but also its own sensitive information.
It just goes to show that any organization can experience a breach. That doesn’t mean there’s no way to increase confidence in your security. In fact, if you handle things correctly, you can lower the chances of experiencing a breach significantly. Many of the aforementioned attacks happened because the affected companies were not vigilant about maintaining their security.
Check out this infographic on how some infamous cyber-security vulnerabilities of 2014 affected data:

Photo Credit: incapsula.com
Why You Need a Technology Estate and Security Maintenance Team
Managing the technology estate of a large organization or company is difficult enough, and that’s before said company goes through any kind of growth or restructuring. Because of this, you absolutely need a dedicated team working full time on maintaining technology systems, security and all IT-related tasks.
If you’d prefer not to have the team on your own payroll, you can hire a third party to handle the work. There are plenty of security providers out there that specialize in network and infrastructure monitoring, software and hardware maintenance, and much more.
Without delving into the particulars, one of the more obvious roles of a security team would be to ensure all software and hardware is up to date and running smoothly. There tends to be a lot more vulnerabilities in software applications and systems that are outdated. To improve security, it’s best to install all upgrades and security patches as soon as they are available.
The problem is this can be difficult to stay on top of if you already have a long list of other responsibilities. Updating a system becomes a lower priority, and security suffers by proxy. If you have a full-time team managing updates, there’s a lot less to worry about.
Tighten up Data Policies for Everyone
There’s only one way to protect sensitive data, and that’s to lock it down as much as possible. Of course, encryption is always necessary when it comes to data storage, but external storage and how it’s used is just as important. For instance, employees should never be allowed to transfer confidential data to an external storage device – such as a USB drive – and take it with them off the job. This is even more crucial in environments where employees are allowed to take their work home, or when a company has BYOD (bring-your-own-device) policies in place.
The solution to this is to provide employees a portable work device that is encrypted and has access to the appropriate systems, both locally and remotely. If they need to work from home they can simply take their work device with them, and all sensitive data remains protected and secured behind active security protocols.
As for encryption, it should be used on any and all devices used within the organization, including mobile devices, laptops, desktop computers, external hard drives and storage options, and anything else that fits the bill.
Educate Your Team, and Plan for Emergencies
Unfortunately, breaches are inevitable no matter how secure a system, network or device is. What happens during and after a breach, however, makes all the difference. That’s why it’s extremely important that you educate and train your team for emergencies, even if they aren’t part of your IT or security department.
Criminals are constantly using a bevy of tools to gain access to systems and information they shouldn’t, like ransomware, Trojans and keyloggers, phishing emails and websites, DDoS attacks and even the occasional brute force attack. All employees should be trained to spot problems, or at the very least should be able to recognize when something shady is happening so they can file a report.
Educating employees will also help protect them off the worksite while they’re browsing from personal computers and devices. It’s still possible for criminals to attack employees by extracting knowledge and information from them when they’re not at work.

Photo Credit: neomam.com
Always Browse Behind a VPN
Firewalls are a no-brainer when it comes to security, but few know that browsing should always be done from behind a VPN or virtual private network. A VPN is designed to mask the true IP address of a system, protecting both the anonymity and privacy of those using it.
Why is this important for an organization or business? It keeps the activity and data of all employees protected from outside prying. Most VPNS also offer an advanced form of security to encrypt any and all data being transmitted via the system. Data packets are encrypted, meaning even if someone is able to hack into a network or listen to what’s going on, they’re going to have a hard time translating the data without the proper encryption key.

Photo Credit: visual.ly
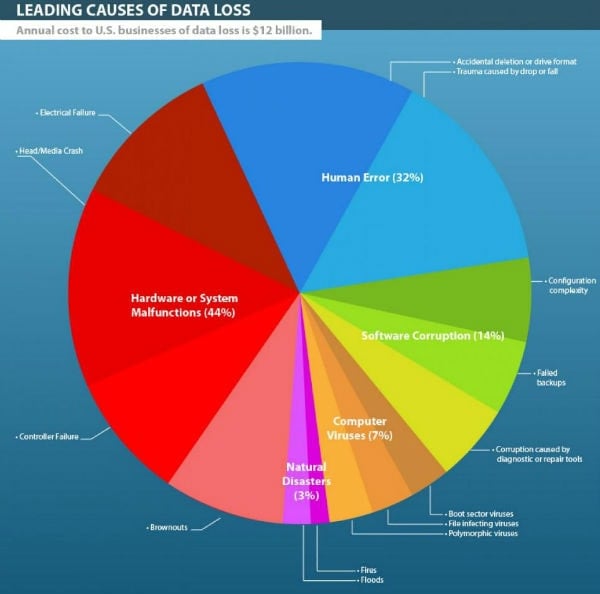
Incorporate a Data Backup Routine
Every business or organization that handles a great deal of data or sensitive information should already have a backup routine in place. That is, should data be lost, backups can be used in place of the originals.
Backups should be given the same care and security because criminals can still use this information if they get their hands on it. There are service providers that will handle all the steps and maintenance for backing up a system. This is the preferred method for many companies, because the service provider will maintain the backups, monitor security and supply the necessary hardware.
This is one of the most important forms of protection you can offer clients. There are many ways criminals can alter or scramble data after they’ve gained access. If you only ever have one copy, after they destroy it you lose it completely. With data backups, at least you have the option to restore data for your clients and employees after an attack.
A Symantec report from 2013 claims that 47 percent of enterprises lost cloud data and were forced to restore from backups. In addition, 66 percent of all organizations attempting a backup had their operations fail. Furthermore, 13 percent of those instances were caused in the first place by hackers who deleted the data.
The takeaway here is that no matter where your data is stored, backups are always necessary and should be a regular part of your security protocol.
Boost Confidence in Your Digital Security
Following these steps won’t completely prevent a breach, but they can help you prolong it from happening. Having a strategy in place for your team and backups to access during and after an attack will help your damage control process significantly, as well.
Just remember, anyone can become the target of a hacker and when they want in, it’s incredibly difficult to keep them out. Security is no joke, so do what you can to bolster it and improve confidence.
Sarah Landrum is the founder of Punched Clocks. Follow her on Twitter @SarahLandrum.