Friday Fun Blog: Chocolate Farts Edition
February 13, 2015
Friday Fun Blog: The After School Special Edition
February 20, 2015Have you ever been to a computer retail store and the sales associate pitches you an anti-virus software and one of the choices is something called “Kasperksy?”
Have you then thought, “What’s a Kaspersky?” or something similar? Well, that weird Russian company that you ignored for the bloated Norton anti-virus has just made a huge discovery.
That discovery, I imagine, happened in a dusty Moscow lab around cups of steaming borscht, and brought more light to an organization known as “The Equation Group.” No, not that group of nerds from your high school that went the Mathletes final—these guys are geniuses. Who, apparently, have forgotten how much time Russians have.
Let’s give you a brief background of The Equation Group: Around 2002-03, Equation started placing unique encryption algorithms (see: malware) to spy and obtain information from certain organizations and countries. Those algorithms, along with other various techniques is why Kaspersky named Equation as such.
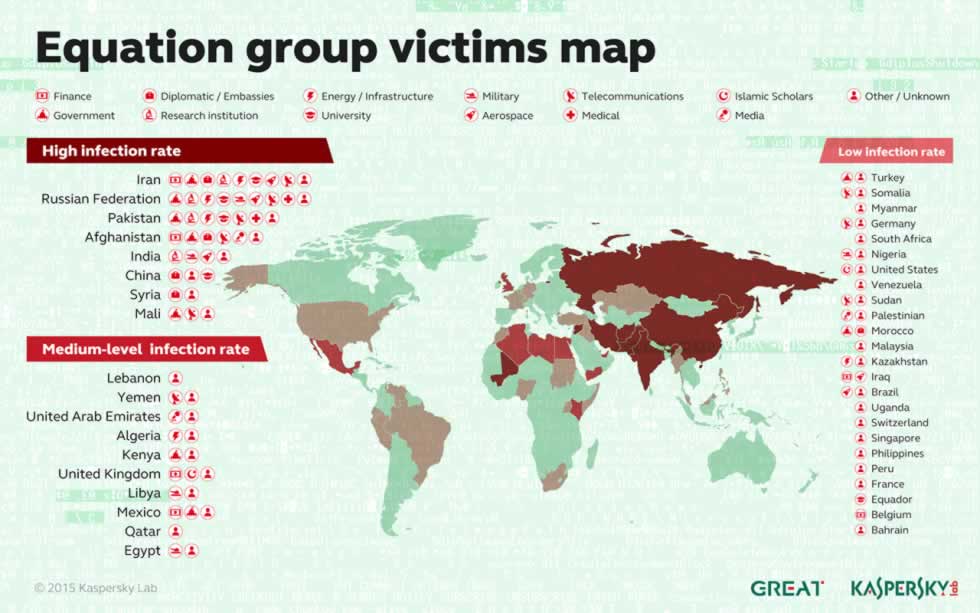
Kaspersky discovered 500 infections in at least 42 countries done by the Equation Group—the big players being Iran, Russia, Afghanistan, and India. The smart and dangerous thing, however, how the virus was designed. There’s a built-in self destruct mechanism that was coded directly into the malware, so Kaspersky believes the number of documented infections they have discovered only skims the fat off of Equations cauldron of malware-soup.
If you’re beginning to wonder just how impressive Equation Group is, check out what they’ve been able to accomplish:
- Use of virtual file systems (Check out this attack on a Belgian firm)
- Storing infected files in a computer’s registry—impossible for an anti-virus software to detect
- iPhone users were redirected to exploited Web pages (both iOS and OS X have been infected)
- Uses of over 300 domains and over 100 servers which hosted a command and control infrastructure.
- The ability to map air-gapped networks without the use of the internet using USB stick-based malware.
- Finding a way to bypass code-signing restrictions in Windows
These guys are legit. And Kaspersky believes the only organization to have this much intellectual power (and wealth to pull it off) is the National Security Administration (NSA) of the United States. But they don’t have fool-proof proof… but, come on—right? We kind of know.
You can read more about the NSA implications in this beautifully detailed article from our friends at Ars Technica.
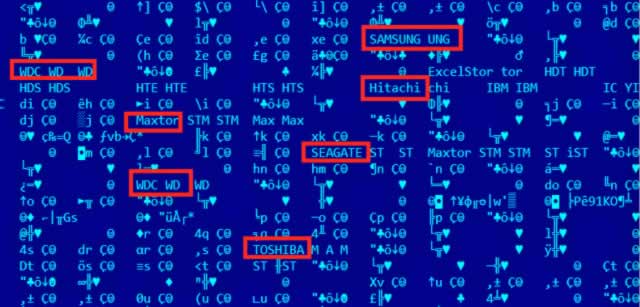
But before you do that, check this scary notion out: Equation Group has placed their malware in hard drives from the world’s leading manufacturers, such as Western Digital, Samsung, Toshiba, Seagate, IBM, etc. The malware rewrote the hard-drive firmware of infected computers, which was never before seen before Kaspersky just discovered.
In case you didn’t know—like me—it’s just short of impossible for someone not involved with the manufacturer to reverse engineer a hard drive, read the existing firmware, and create malicious versions.
Costin Raiu, the Director of Kaspersky’s Global Research & Analysis Team, said, “”This is an incredibly complicated thing that was achieved by these guys, and they didn’t do it for one kind of hard drive brand. It’s very dangerous and bad because once a hard drive gets infected with this malicious payload it’s impossible for anyone, especially an antivirus [provider], to scan inside that hard drive firmware. It’s simply not possible to do that.”
Not possible for mere mortals, at least—not for Equation Group.
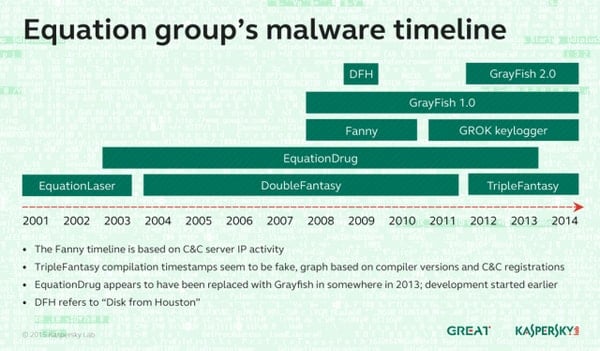
The Malware Associated with The Equation Group
While not linked to Equation Group until recently, some of their malware has been found and named before this report. The scope of their work is amazing and unique:
- EquationLaser — discovered and used as an implant most commonly throughout 2001-04
- Double Fantasy — a Trojan virus which determined if the infected machine was the intended target.
- EquationDrug (Equestre) — re-flashes hard drive firmware and uses virtual file systems to hide stolen data.
- GrayFish — EqationDrug on steroids. This bypassed Windows code-signing requirements. So complex that Kaspersky still doesn’t fully understand it.
- Fanny — not as funny as it sounds. Fanny is a worm that specialized on sensitive air-gapped networks.
- TripleFantasy — Used in tandem with GrayFish, which featured a nice backdoor for malware to slip in.
The Mistakes: Equation Group Was Not Perfect
In any type of coding, mistakes are inevitable.
Kaspersky found machines that were still infected by malware that was at least 12 years old in Russia, China, Iran, and India.
It was in these machines that Kaspersky was able to glean developer account names, variable names, and other such things that were left in the malware.
Kaspersky, again, threw a few rib-shots at the NSA saying that the time and money it would take to produce these types of malware would have to come from a nation-based organization with unlimited money to throw at the project.
As of the time of this publishing, the NSA has contacted Ars Technica with this statement:
We are aware of the recently released report. We are not going to comment publicly on any allegations that the report raises, or discuss any details. On January 17, 2014, the President gave a detailed address about our signals intelligence activities, and he also issued Presidential Policy Directive 28 (PPD-28). As we have affirmed publicly many times, we continue to abide by the commitments made in the President’s speech and PPD-28. The U.S. Government calls on our intelligence agencies to protect the United States, its citizens, and its allies from a wide array of serious threats – including terrorist plots from al-Qaeda, ISIL, and others; the proliferation of weapons of mass destruction; foreign aggression against ourselves and our allies; and international criminal organizations.
We will keep you updated on this story as it develops and remember to keep security in mind when choosing any type of IT software as security flaws are everywhere. You want to do your due diligence to ensure that you’ll be protected.