Friday Fun Blog: Phallic Fun Edition
March 13, 2015
This Week in Getting Hacked: Access the Mainframe Edition
March 19, 2015Cyber-security problems seem to be a hot topic any time business and data are spoken in the same sentence. We have written at length in the past about several big business cyber-security risks—detailing what happened, what should have been done, etc.
While the cyber-security flaws seem to catch all the attention, little seems to be known on how it happens in the first place and what could have happened to prevent it.
Michael Kassner of TechRepublic.com says, “defending against cyber attacks is a complex, thankless, and never-ending job.” But hopefully by the end of this article, we may receive some gratitude.
Attacking the Supply Chain
Do you know those cool guys over at Huawei? The ones that make all those cool technologies that never seem to come to America? Well, they give a great introduction into our topic in this video put together by their Chief Security Offier, John Suffolk:
Cyber-security risks are under fierce investigation and they seem to happen most commonly for these big businesses during the supply-chain phase. The security there just isn’t up to par. Many of the breaches talked about above began with the attackers finding their way into the company’s supply chain.
Take this study done by CERT-UK entitled “Cyber-Security Risks in the Supply Chain” where they describe, “For any modern organization, physical supply-chain management already presents numerous complex challenges in understanding exposure to risk. The added complexity of cyber security risks only amplifies this, regardless of their position within a supply chain.”
So what’s next?
Not Much Attention Paid to the Digital Supply Chain
The paper mentions that most businesses have the physical side of their supply chain in tight control. Typically, that’s how businesses have been operating for years. There’s tried and true practices for that side of the business.
But the digital side is different. It’s still relatively new in the grand scheme of business. And companies still haven’t quite nailed down the security of it. And that’s the problem.
Their existing cyber security, not necessarily related to their supply chain, has been reliable and efficient—which could lead to a false sense of security. The supply chain, then, is often overlooked, becoming the weakest cyber-security link.
Understanding the Supply Chain Cyber-Security Risk
Business owners, then, should research a better understanding from, as K2 Intelligence’s Jeremy M. Kroll puts it, “from the outside-in.”
Kroll explains that companies lack the knowledge of what and who they are going up against. By understanding their attackers and their tactics, companies will have a leg up on the type of vulnerabilities their companies have and how they are going to fix them.
This deeper understanding, Kroll offers, should take place not after a deal is done with a supply chain partner, but before it. Investigate the whole operation from the perspective of the attackers.
But most importantly, businesses should know where their sensitive data resides outside their network. This is the most crucial step in protecting themselves against an eventual threat.
Business can do that, Kroll states, by compiling information and “risk profiles” of themselves and their business partners to ensure that all parties involved are adhering to cyber-security practices and standards that will benefit and protect themselves, their partners, and the customers.
Where Do Third Parties Store Data?
It’s safe to say that the most crucial aspect of understanding the supply chain cyber-security risk is understanding a business’s third party partners—and more importantly, what they do with a business’s data. 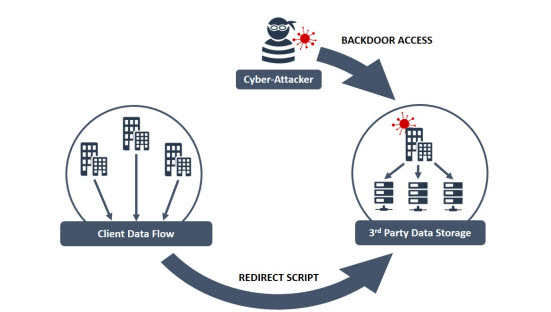
Businesses sometimes outsource their data to third party companies who store, process, aggregate, and broker the information, according to the CERT-UK study.
This data is then passed around (sometimes to direct competitors) and anywhere throughout this process, if the proper security measures aren’t in place, the data can be compromised.
This data is not, although usually, just sensitive customer information—but it could also be sensitive business information such as their structure, strategies, etc (take Sony’s major security hack, for example). For attackers, business data could prove to be far more valuable than customer information (if fraud is found, blackmailing can happen), so all avenues must be secured—not just what makes the news, which is typically all about leaked consumer information like credit card and bank accounts.
How Do Supply Chains Get Hacked?
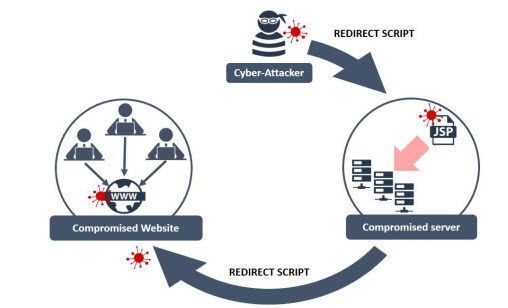
There are countless ways supply chains can be “cyber-hacked.” The CERT-UK study describes some real life examples such as:
- Adding a Trojan virus to Industrial Control System Software (ICS) – Attackers replaced legitimate software files with malware files, which were downloaded by clients.
- Compromised legitimate sites through the website developer – The study describes, “rather than compromising a number of legitimate sites individually, the attack targeted the core script of a website template designed by the creative and digital agency”
How to Mitigate Supply Chain Cyber-Security Risks
What it all boils down to is understanding where your business’s data resides and what your partners and clients are doing with it. It takes detailed preparation and well-vetted security systems of parties involved to ensure reliable cyber-security.
Since cyber-attacks happen from virtual safe havens from the attackers, sometimes cyber-security gets overlooked as part of a solid business structure. Today, however, as more and more businesses are getting attacked, something needs to be done.
These factors in particular, according to CERT-UK’s study, need to be fixed immediately:
- The lack of common risk vocabulary
- Inadequate data and information sharing across the supply chain
- Inappropriate or non-existent business resilience strategies
The first step towards doing this is bringing to life a supply chain risk assessment process that engages as many, or all, members of the supply chain process as possible.
While complex, this is a surefire way to ensure cyber-security from where it’s weakest. A strong, secure supply chain will also charter more business, so while the upfront costs of implementing cyber-security procedures may seem complex and daunting, it has the priceless benefit of knowing your and your client’s information is safe and secure—not to mention the reputation boost as well.
All images courtesy of cert.gov.