
Disaster Recovery Part 1: Possible Disasters & Mission Critical Systems
August 10, 2017
Disaster Recovery Part 2: Common Failures & Predictable Recovery
August 24, 2017Welcome back to ‘This Week in Getting Hacked’—the world’s greatest cybersecurity-related link dump! Each week, we bring you the best news stories from the cybersecurity field, letting you know who’s getting hacked, who’s hacking, what data is leaking, and about what you should take with caution. So strap in, change your password, and let’s find out who’s getting hacked this week!
On to the links…
So the warrentless surveillance of US citizens under Section 702 of the Foreign Intelligence Surveillance Act (FISA) is set to expire at the end of the year, unless Congress reauthorizes it. This rule allows law enforcement to listen in on conversations between people in the US and foreign countries, with the reasoning being that it’s for national security.

However, numerous declassified documents revealed that there is a huge amount of overreach in terms of data being captured and searched, often times on unwitting and innocent civilians. The wording in the law prohibits “intentional collection” of US citizens’ data, but the NSA and FBI have the repeatedly overstepped their boundaries.
If you’re fishing for tuna, sometimes you might catch a grouper or two in your nets. President Trump currently supports the reauthorization of Section 702.
If anybody knows about the value of privacy in an online world, it’s Valerie Plame, a former CIA operative covertly working overseas to stop bad people from getting nukes. Her cover was blown in a 2003 article in The Washington Post, and her private life hasn’t been the same since.
Kinda tough to be a spy when everyone knows you’re a spy. In any case, Plame is now an advocate for privacy and security, speaking at the Cloud Identity Summit in June:
“[Surveillance] is an enduring fact of modern life. Americans [seem to be] cool with Americans seeing their stuff. I don’t think they understand implications. When they have that much information, historically we have seen that they don’t handle it as carefully as one might hope,” she said.
You can control “adult toys” anonymously through the Tor network, apparently. Invading all sorts of privacy.
Bill Burr (nope, not that “Bill Burr”), a former National Institute of Standards and Technology manager, now regrets his suggestions for how people should create passwords for their accounts. His recommendation of using characters, different cases, and numbers wasn’t exactly the best advice when it comes to passwords, and actually resulted in people using different variations of the same characters which makes it pretty easy for hackers to crack your password.
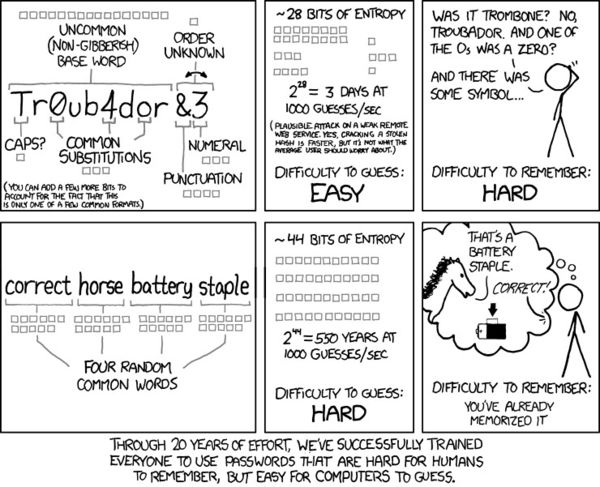
Essentially, “p@s$w0rd” isn’t as strong as a random group of words like “horsebluetorchpancake”. DOH JEEZUS.
Ships are back to using radio for navigation since it’s super easy to hack a ship’s GPS and sail it directly into a dock or whatever.
And finally…
The Stingray surveillance system is one of the most powerful tools law enforcement has at their disposal, allowing them to gather communications, voice, and GPS data with EXTREME accuracy. A few apps out on the market purport to be able to disrupt that ability, but it turns out that’s not the case; those apps are basically useless, and even though they may detect certain stingray properties, they’re easily bypassed through other methods.

So the old saying goes, “If law enforcement wants to get you, they will.”
That’s it for this week! Make sure you change your password to something like “carriagemarketburncrumb.“
