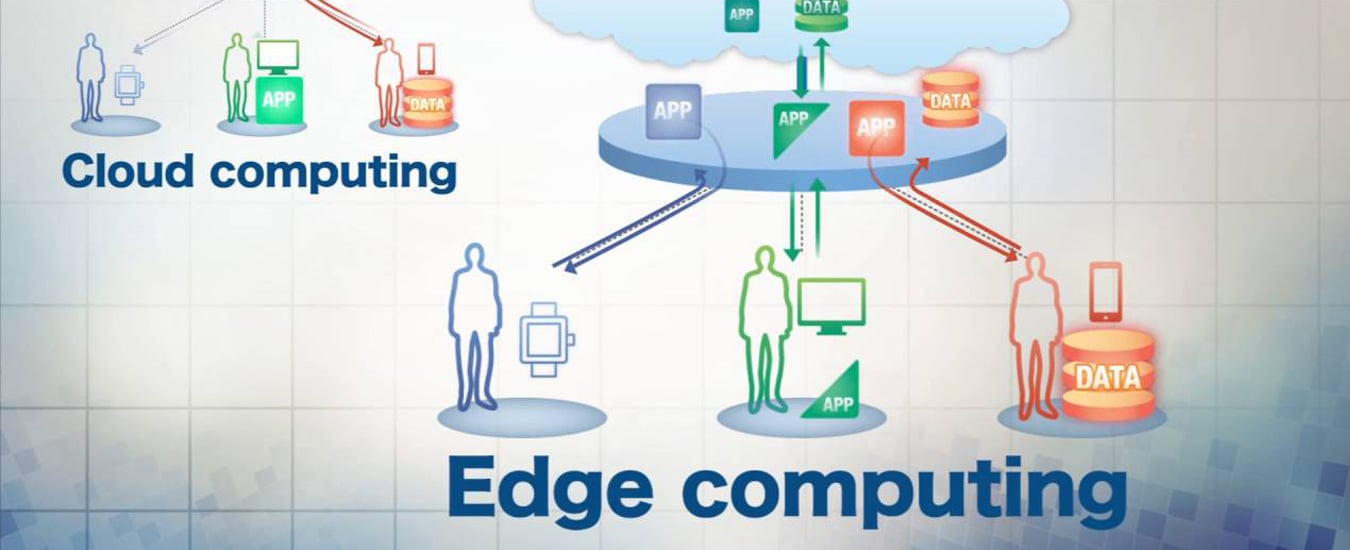
What Is Edge Computing and Why Is It Taking Over?
October 10, 2017
6 Tips For Anyone Seeking To Engage a Tech Staff
November 8, 2017Welcome back to ‘This Week in Getting Hacked’—the world’s greatest cybersecurity-related link dump! Each week, we bring you the best news stories from the cybersecurity field, letting you know who’s getting hacked, who’s hacking, what data is leaking, and about what you should take with caution. So strap in, change your password, and let’s find out who’s getting hacked this week!
On to the links…
The Russian government is sneaking around behind closed United States doors again (WSJ paywall). This time, those pesky Russian hackers stole NSA data on U.S. cyber defense. Yep. Hackers stole plans on how to stop hackers. This is about how we all expected U.S. data security to go, right?

Pictured: Russian Spy Sneaking Around U.S. Firewalls
Not only did they steal information on how the U.S. stops cyberattacks, but they also stole information on how the U.S. does cyber attacks. Let’s try a sports analogy. The Russians are the New England Patriots. This is “Spygate” part 2. This time Patriots (Russians) have stolen both the offensive and defensive playbooks from the United States. Oh, and the AFC Championship game is right around the corner. Great.
A new study performed on SMBs reports that 66 percent of them would close if the experienced a data breach. Yikes!
The VIPRE report suggests that 23 percent of SMBs were under cyber-attacks on a daily basis and that the entire 66 percent would shut down regardless of whether or not the systems were compromised.
Most SMBs have to shovel nearly $700,000 to mitigate the damage. No wonder 60 percent of small business can’t sustain their business half-a-year after a cyber attack.
Some of the more popular paid VPN services claim that they don’t store logs of your browsing history while using their service. That’s why they’re popular. However, one of the more popular ones, “PureVPN” recently handed over that non-existent browsing history to the FBI so they could catch an Internet stalker.
Here’s PureVPN’s privacy policy:
We Do Not monitor user activity nor do we keep any logs. We therefore have no record of your activities such as which software you used, which websites you visited, what content you downloaded, which apps you used, etc. after you connected to any of our servers.
Well, apparently they do exist. Just another reason to trust no one and to abandon the cyber-world and live out that dream of coming a mountain-person deep in the Yukon territory.
Concealing hacking equipment in the ceiling of a prison cell would be way down the list on a “Family Feud” question on the matter. Don’t tell that to inmates Johnston & Spriggs of the Marion Correctional Institution in Ohio.
These inmates set up and hid hacking equipment in the ceiling of their cell where they used knowledge of computers learned in prison to hack the prison itself. There’s something wrong here.
In case you somehow missed it, here’s the trailer for Star Wars: The Last Jedi:
And finally…
RIP the Windows Phone. I know, I know, it’s not really hacking news, but I couldn’t just sit silent about it. Here’s a touching tribute. Try not to cry.

