This Week in Getting Hacked: Cyber-Grenade Edition
November 10, 2016
This Week in Getting Hacked: Are We Still Talking About Ashley Madison Edition?
November 18, 2016Ransomware is a type of malware (malicious software) that cyber criminals use to block people and businesses from accessing certain files on their computers or networks. The victims of such an attack either need to pay a ransom to unlock their files, or risk losing those files forever. The money is usually sent via an untraceable online currency, so the criminals never risk getting caught.
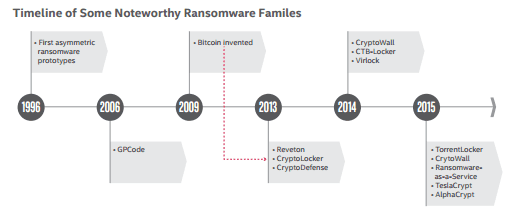
Even though ransomware has been around since the 1990’s, it did not become popular until bitcoin was invented.
Since bitcoin became the first decentralized digital currency, there has been no authority that can manipulate the currency, or force a transaction to be canceled for any reason. Bitcoin has made it possible for cyber criminals to collect a ransom without exposing themselves, making it the perfect currency for carrying out a ransomware attack.
Then, in 2014, we saw the rise of Ransomware-as-a-service (RaaS), which meant that anyone could perform a ransomware attack, even someone without any programming skills. RaaS has allowed a lot of people to make a lot of money on these attacks.
In 2015 alone, there were more than 2,400 ransomware attacks reported to the FBI. The FBI has estimated that those victims lost more than $24 million in that year. Since then, ransomware attacks have been growing at a rate of 9 to 20 percent every month. Now, the average ransom has grown to $679 per attack, up from $294 per attack in 2015.
What Are the Different Types of Ransomware?
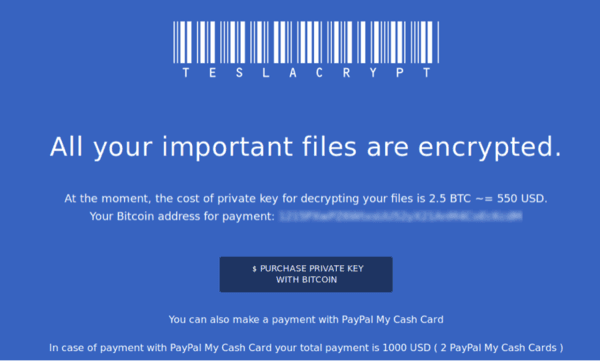
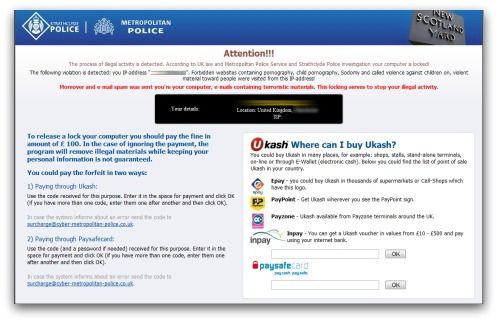
There are two different types of ransomware; the first kind is called a “locker,” which locks the computer screen until a ransom is paid. The second kind is called crypto-ransomware, which encrypts the actual files on the computer until users pay for a key to decrypt them.
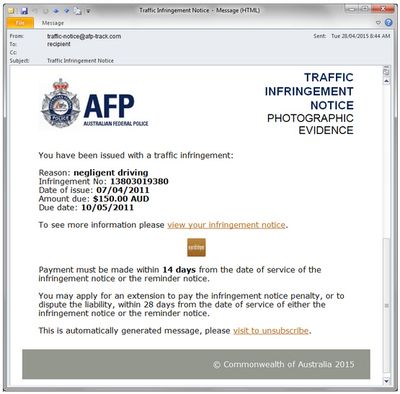
Locker ransomware disables a victim’s computer screen by replacing it with an image that looks like an official police warning about illegal activity. These warnings use official police and government logos to scare users into paying a fine within a certain time limit in order to unlock their computer.
A lot of these victims end up paying the ransom out of fear that the police might have some evidence that they were somehow complicit in an illegal activity. A lot of other victims recognize that it’s a scam, (because there is no way a police department would ransom a criminal) but they end up paying the ransom because they just want to restore access to their files.
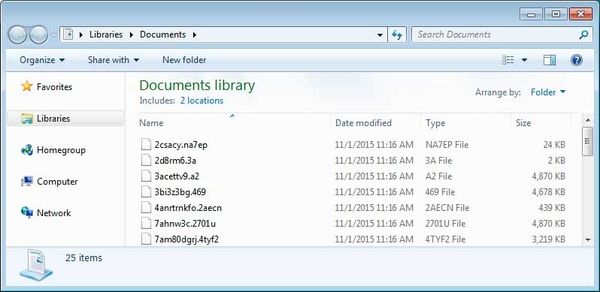
Crypto-ransomware is very similar to a locker ransomware. They both block the user from accessing any of their files, but crypto-ransomware takes it one step further by also encrypting the user’s files. That means that even if a victim was able to remove the ransomware, their files would still be inaccessible until a decryption key could unlock them.
Crypto-ransomware uses an asymmetric key cryptography, which means it uses two keys; one to encrypt the data, (the public key, which can be found in the encryption) and another key to decrypt the data (the private key, which is only in the hands of the attacker). By using multiple keys, ransomware can encrypt files without giving away the decryption key.
Some versions of crypto-ransomware can even compress files, password protect individual files, and even encrypt the filenames, so it’s impossible to know which files are important.
How Malware Works
The majority of ransomware attacks originate with spear-phishing email scams. These fake emails impersonate trusted sources that are sending bills, invoices, resumes, traffic tickets, and even tax returns. When a user clicks on a bad link in the email or downloads a bad attachment, they also download the ransomware onto their computers and networks.
Users can also accidently download ransomware by clicking on bad advertisements. This is called malvertising, and these ads can be found on even the most trusted websites. In fact, cyber criminals have got so good, that users don’t even have to click on the ad anymore.
All a user has to do is visit a bad website, and the ransomware will be automatically downloaded to their computer without their knowledge. That is called drive-by downloading, and according to FBI Cyber Division Assistant Director James Trainor:
“These criminals have evolved over time and now bypass the need for an individual to click on a link. They do this by seeding legitimate websites with malicious code, taking advantage of unpatched software on end-user computers.”
How to Prevent Ransomware
There are many ways to protect yourself from a ransomware attack, but none of them is foolproof. So, it is important to take preventative measures and remain vigilant.
Phishing
Since the majority of these attacks begin with a phishing email, it is important to be wary of any email that comes from an outside source. This means everyone on your network should know the dangers and signs of phishing emails. And, for even more protection, you can also set up an advanced email spam filter to catch any potentially harmful emails.
Backups
No ransomware attack can lock you out of your data if it is backed up properly. That is why it is important to follow the 3-2-1 rule, which means you should have at least three copies of your most important files in two different formats and one additional copy that is stored in an off-site location.
This means that you also have to back your files up on a regular basis. So, make sure it is a part of your routine, or put someone in charge of managing those files. One easy option is to use cloud or colocation services, where you can have a backup server that syncs your files.
Antivirus
The best way to avoid a drive-by download is to use a good antivirus software. There are many options out there, just make sure to keep your antivirus on at all times, and do not ignore the warnings that it gives you. This includes the update reminders that always pop up. These updates contain patches that guard against the newest malware attacks. If you ignore them, your system will be just as vulnerable as a system without an antivirus program.
What to Do If You’ve Been Infected with Ransomware
Once you have been attacked, there is not much you can do. If you have a good backup, then you can wipe your system and start over again. Just make sure that the malware is gone before uploading the backup files on your system again.
If you do not have backup files, it still might not be a good idea to pay the ransom. The FBI doesn’t suggest that victims pay the cyber-criminals. As FBI Cyber Division Assistant Director James Trainor says, “Paying a ransom doesn’t guarantee an organization that it will get its data back—we’ve seen cases where organizations never got a decryption key after having paid the ransom. Paying a ransom not only emboldens current cyber criminals to target more organizations, it also offers an incentive for other criminals to get involved in this type of illegal activity. And finally, by paying a ransom, an organization might inadvertently be funding other illicit activity associated with criminals.”
They also say that paying a ransom could cause them strike you again, and ask for more money this time.
If you are a victim of a cyber-attack, you should contact your local law enforcement agencies and the FBI or the USSS (United States Secret Service) field offices immediately. Giving them your information can help them track these criminals down, and they will be able to walk you through the basic steps you need to take.
Main photo credit: fireeye.com