What is the Domain Name System or DNS?
August 8, 2019
How Cloud Services Help the Environment
August 14, 2019A Software-Defined Perimeter is an approach to computer security that micro-segments network access. It establishes direct connections between users and the resources they access. A Software-Defined Perimeter focuses on three main pillars:
Zero Trust
Identity-Centric
It operates around a user’s identity and not a user’s IP address.
Designed for the Cloud
It operates in cloud networks and provides expandable security. SDP Software authenticates and authorizes all endpoints trying to access a particular infrastructure. It also makes unauthorized networks inaccessible. This reduces the surface area of attack by hiding network resources to unauthenticated or unauthorized users.
Network Perimeter Security Definition
Network security refers to a boundary between a local and private owned-and-managed side of a network.
What Are the Uses of SDPs?
SDPs have many uses, including:
SDPs Support Many Devices
SDPs can authenticate PCs and laptops, as well as mobile devices and IoT (Internet of Things) devices. SDPs restrict connections from invalid or unauthorized devices.
SDPs Prevent Broad Network Access
SDPs prevent individual entities cannot access broad network subnets or segments. So, devices can only access specific hosts and services that are policy permit. This reduces the attack surface of the network. It also prevents vulnerability scanning by malicious software and malicious users.
SDPs Support a Wider Risk-Based Policy
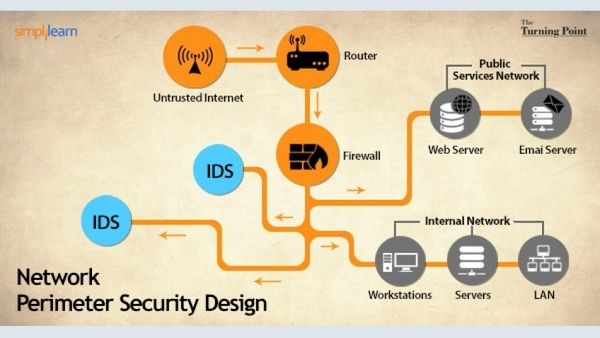
Credit: simplilearn.com
SDP grants access based on specified risk criteria. These include new software, threat intelligence, and malware outbreaks.
SDPs Can Connect Anything
Software-Defined Security allows connectivity to IT resources required by staff members. It also eliminates mounting hardware costs and burdensome management requirements.
SDPs Enable the Control of Access, Services, and Applications
SDPs are adept in controlling which devices and applications can access a given service. This reduces the surface of attack and prevents malicious malware or users from connecting to resources.
How Does a Software-Defined Perimeter Work?
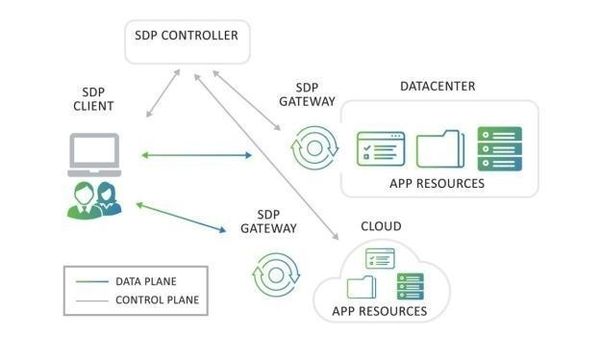
The first component needed to access a resource (entity) or an application is a client. The entity has no DNS entry, which is a significant security feature. So, it remains hidden and has no direct access. Rather, the client is given an agentless or SDP-enabled means of communication with second components.
This is an SDP controller which umpires connectivity between users and IoT devices. The controller contains a limited list of authorized users. It also has a list of registered devices.
The controller understands the security state of the device and who the user is by communicating with the client. This information is then verified by checking it against a roles-based access control. After verification, security certificates are exchanged.
The controller then lets the gateway know that a client will send an authenticated communication. The gateway and the client establish secure communication.
The Software-Defined Architecture creates a strict access method for particular resources and applications. There is also a reduced surface of threat because target entities remain hidden, and the controller must verify users. Software-Defined Firewall eliminates credential theft, internal network attacks, malware, and man-in-the-middle attacks.
Use Cases of Software-Designed Perimeter
Below are some use cases of SDP:
DevOps
SDP provides secure access that enables DevOps users to isolate workloads and access key resources.
Network or Application Segmentation
The perimeter security group minimizes the attack surface and malware propagation inside cloud environments and data centers.
Simplified BYOD Access
SDP provides secure, easy, and direct access to cloud applications. It also enables easy access to resources from a user’s preferred device.
Privileged and Third-Party User Access
Perimeter security partners enable privileged and third-party access to systems from any location.
SDP Framework
SDP technology enables secure perimeter by using policies that isolate service from insecure networks. The CSAs SDP does three things:
- It provides an air-gapped, provisioned, and on-demand network.
- It segments network resources into defined network perimeters.
- It authenticates devices and users before authorizing the device/user combination before connecting to an isolated service. SDP framework ensures that unauthorized devices and users cannot connect to isolated services.
Once authentication is complete, trusted devices receive a unique and momentary connection to a network infrastructure. Software-defined management allows companies to streamline operations concerning application security and user authentication.
Models of SDP Deployment
The models of SDP deployment focus on how they structure interactions among gateways, servers, and clients. The main approaches taken when implementing SDP technology include:
Client to Gateway Deployment
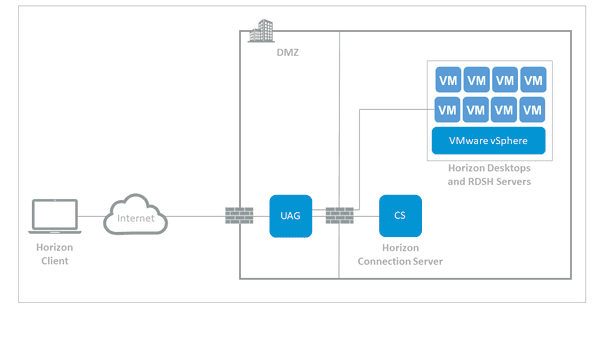
Credit: vmware.com
Client to Gateway deployment places servers behind an Accepting Host. This serves as a gateway between the clients and the protected servers. The Client to Gateway is also deployed inside an SDP network to minimize lateral movement attacks.
Lateral movement attacks include application vulnerability exploits, server scanning, and man-in-the-middle attacks. Client to Gateway is also deployed online to mitigate attacks and isolate protected users from illegal users.
Client to Server Deployment
The Client to Server Deployment and the Client to Gateway Deployment are similar. The only difference is that the server protected by the SDP in the Client to Server deployment is the system that runs the Accepting Host. Choosing between the Client to Server Deployment and the Client to Gateway implementations depends on various factors. These include:
- The elasticity of the servers,
- The adaptability of the software-defined cloud servers to change,
- And the number of servers needed to safeguard the SDP.
Client to Server to Client Deployment
Client to Server to Client deployment depends on a P2P (peer to peer) relationship. Clients can use the P2P relationship for applications, including video conferencing, chat, and IP telephony. In this implementation, the SDP obscures the connecting clients’ IP addresses. The server acts as an intermediary for the clients.
Server to Server Deployment
Server to Server implementation uses servers that:
- Provide API (Application Programming Interface) over the internet,
- Have a high protectability from unauthorized devices and users on the network,
- Include a simple SOAP (Simple Object Access Protocol) service,
- Include an RPC (Remote Procedure Call), and
- Include a REST (Representational State Transfer) service.
Server to Server deployment use servers that offer any of these applications to communicate between the initiating host and the accepting host.
In contemporary society, there are inadequacies of up-do-date perimeter designs. Companies have been exposing their services, including APIs, RDP, and HTTP/S. Even with added layers of security; hackers can still bring down or infiltrate services through security attacks.
SDPs are capable of preventing such attacks by preventing unauthorized access. They maximize user’s security by enhancing security through their premier technology center. SDPs also obscure services online until it is necessary to allow users to access the service.
Well, what are you still waiting for? Get and SDP today and change how you expose your services. Remember, if hackers cannot see you, they cannot hack you.
Featured Image Credit: securityboulevard.com