
The Next Big Thing in 2020 – CRM Applications for SMEs
January 22, 2020
Top 5 Reasons Why Your Company Should Be Data-Driven
January 28, 2020The financial losses from cyberattacks in 2018 resulted in an estimated $45 billion in losses.
Yikes.
This is an outcome of two reasons.
Second, many targets of cybercriminals aren’t prepared for the assault. Whether by ignoring the existing threats in cyberspace or not investing enough in cybersecurity strategies, decision-makers are leaving their businesses exposed.
The outcome of this decision is well-known: $45 billion, as well as millions of exposed credit card numbers, names, phone numbers, addresses, and emails.
Don’t let this happen to you. You’ve invested a lot of effort and money in creating a business of your own, so throwing it all away by ignoring cybersecurity seems unreasonable, at least.
That’s why go over the following 4 excellent points to know how to create a working cybersecurity strategy for your business and keep cybercriminals at a distance.
Get a Buy-In from Employees
In addition to being your first line of defense against cyberthreats, your employees are also the weakest link in the chain. A lack of training leads to a plethora of unwanted outcomes, including data breaches resulting from weak passwords and violations of organizational cybersecurity policies.
Heck, your strategy to protect your business from data breaches could be working perfectly but can be easily undermined by a single mistake made by a poorly informed or trained employee (yes, train those newcomers very well).
So, you as an owner of your business should make it clear that cybersecurity is not the sole responsibility of the IT team. Every employee should have the ability to protect their organization from cybercriminals, which means they need training.
Make cybersecurity training mandatory for everybody, with a special emphasis on new employees. Cover the most important topics, including malware, brute force attacks, passwords, phishing, social engineering, and more.
To get buy-in, show them the following figure from the recent cybersecurity report by Accenture.
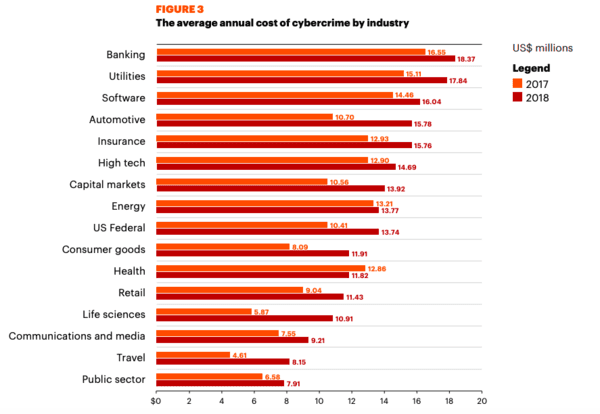
Credit: accenture
Break down the Data and Systems to Protect
First, make sure that your cybersecurity policy covers how to process customer and other business-related data in a manner that keeps it safe. Here’s what to keep in mind here:
- What and how much data you collect in your business processes
- The places where you store all that data, i.e. cloud storage
- Existing data protection measures, i.e. passwords and encryption
- Data backup routines. The frequency of data backup and the stakeholders responsible for this process.
Second, you need to have a good understanding of the systems you use to carry out business processes. These systems are critical for keeping your company alive and include ERP software, accounting, etc.
The cybersecurity strategy should have the following procedures and standards to protect them:
- Clear-cut rules on updating and backing up these systems – as well as who’s responsible for making that happen
- Employee access rights and limits concerning cloud software and other apps running inside your company’s internal network
- Regulations on access to these systems; for example, if you have remote employees, you might want to provide them with security tools like VPN
- User authentication procedures. The organization needs to set rules on how employees identify themselves (password policy, two-factor authentication, etc.)
- Clear instructions on specific incidents and security issues. If the unthinkable happens, your IT team should be able to act quickly to minimize the loss or prevent it altogether.
Include these two sections in your cybersecurity policy so your employees know how it’s going to affect their routines. Moreover, your customers should also have a good understanding of how you’re protecting their private data once they give it to you.
Make Cybersecurity Audits Regular
Constantly checking for vulnerabilities is a good way to keep your data safe from ever-changing threats in cyberspace. To make that happen, write a section in your cybersecurity strategy where you clearly describe the security audits of the existing IT practices and assets.
For example, every audit should evaluate the state of the software and hardware employed for cybersecurity as well as employee compliance with the existing cyber policies and procedures.
While we’re on the subject of audits, demanding them from business partners and vendors is also a good idea. It’s possible for your company’s data to get exposed because of a mistake that comes from an external stakeholder, so consider demanding IT audits from partners.
One good way to make that happen is to request them in contracts. For example, consider making this a mandatory condition of cooperation before signing a contract with a vendor or a partner. Not only you’re making your data safer, but also protecting yourself from liability in case if a partner makes a critical mistake.
Describe How to Report Risks
It’s not uncommon for cybersecurity managers to be surprised by how much they don’t know about their companies when creating a comprehensive risk reporting. Often, they discover an endless number of problems, including a lack of reliable inventory of employees, hardware, software, databases, access privileges, and partners.
One common reason for that is many companies tend to manage mission-critical assets locally, without relying on cybersecurity specialists at a head office.
This Mckinsey report on cybersecurity described a number of real examples where cybersecurity specialists weren’t even aware of the fact that serious risks weren’t reported and exposed lots of sensitive data. Here’s one of them:
A large manufacturing organization used third-party companies to install critical production components in their factories. These devices were connected via inregistered online interfaces, which resulted in a major exposure of the entire manufacturing environment to cyberattacks.
In other words, if hackers got access to this data, they would have had a clear overview of the company’s IT systems (industrial control tools, IoT devices used in production, etc.) as well as the operational technology.
That’s why your cybersecurity should describe how to implement a holistic risk report to make this information available to all decision-makers. The above-mentioned McKinsey report offers a solution: a cyber risk dashboard. It summarizes the risk management chain by using a few dynamic panels presenting the following:
- The development of the risk’s landscape
- The analysis of the recent cybersecurity-related events and incidents as well as the countermeasures were taken by the company
- The most relevant cyber risks as defined by assessing the risk landscape
- Risk evaluations with recommendations for their mitigation
- A clear and detailed risk mitigating procedures with their statuses.
Here’s an illustrative representation of the cyber risk dashboard, as given by McKinsey.
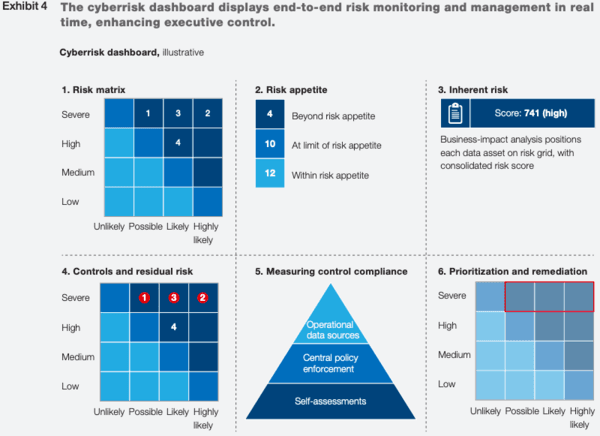
Credit: McKinsey
Cyber risk reporting strategies and tools like these allow companies to be more organized and proactive in their defense. That’s why you consider creating a strategy for this in your own cybersecurity policy as well. While this strategy works best for large enterprises, many elements of this dashboard – the risk matrix, for example – can easily be adopted by small businesses.
Cyberthreats to your data come in a variety of sizes and shapes, so you should be prepared for them. No one wants to see their business struck down by hackers, so your defense against that begins with writing and implementing the cybersecurity policies.
Hopefully, this article was helpful to you to understand where to start protecting the data that keeps your business going. Last advice: begin creating the strategy as soon as possible, as cybercriminals don’t really wait for anyone to get ready for what they have up their sleeves.
Main Photo Credit: Nextgov
